Your NFC capable Android smartphone could be the newest weapon hackers use to steal money from the credit cards in your pocket, researchers find. In a presentation at Hack In The Box Security Conference in Amsterdam, security researchers Ricardo J. Rodriguez and Jose Vila presented a demo of a real world attack, to which all NFC capable Android phones are vulnerable. This attack, delivered through poisoned apps, exploits the NFC feature allowing unethical hackers to steal money from victims’ credit cards anytime the cards are near the victims' phone.
What is NFC?
Near Field Communication or NFC is a short-range contactless communication system that uses wireless data to allow various technologies in in close proximity to each other to communicate without the need for an Internet connection. NFC is the primary technology that allows for features like Android Beam. Android Beam allows Android users to swap pictures or contacts by holding two devices together. NFC technology has been increasingly used in cashless payment systems such as Google Wallet and now Android Pay.
NFC evolved from radio frequency identification (RFID) technology. An NFC chip, which can be found in most Android smartphones released in the last 2-3 years, acts as one one part of a wireless link. Once it's activated by another NFC chip, small amounts of data between the two devices can be transferred when they are held a few centimeters from each other.
How Hackers Can Attack Your Credit Cards With NFC
While there has been much research into NFC relay attacks in the past, these kinds of attacks have often been considered difficult to perform, because it required having two devices very close in proximity to one another. In 2013, however, researcher Michael Roland found that by installing Trojan relay software on a victims' Android phone, the attacker could initiate Google Pay payments using the NFC properties in the victims's device. When Google was made aware of this weakness, they were quick to patch the problem. With this latest research, however, Rodriguez and Vila found that hackers could utilize the NFC property in the victim's phone to steal money from the physical credit cards in his or her pocket, rather than through Google Pay, when the cards come in contact with the victim's phone. If you think of how often your wallet is near your phone, the instance for attack becomes much more probable.
To execute this kind of attack, all the equipment a hacker needs is a POS machine that can accept NFC payments and an NFC capable Android phone running Android 4.4 KitKat or above.
So how do attacks happen? The method is called a relay attack. A relay attack, basically allows the forwarding of an entire wireless communication over a large distance instead of the small distance NFC allows. This is done by having four different players involved, which are known as: the honest prover, the honest verifier, the dishonest prover and the dishonest verifier. In the attack, a dishonest prover and a dishonest verifier act together to cheat the honest verifier and a honest prover. Our verifiers and provers are as follows:
- Honest prover and verifier: your physical credit card and the attackers Point-of-Sale terminal.
- Dishonest prover and verifier: the attacker’s NFC capable Android phone and yours.
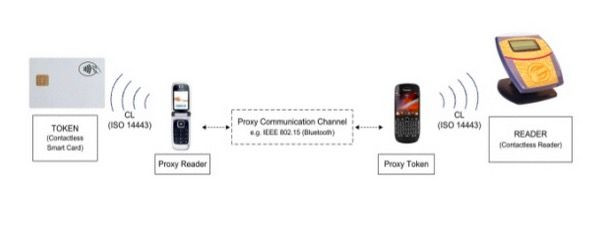
To launch the attack, a hacker needs to makes a desirable app available somewhere on the web or an app market – many times this might be a cracked app you can download for free rather than paying for it. (ex: SC Secret Recorder, $3.50 on Google Play, free as a cracked app). The victim downloads the app, unaware that there is malware embedded in it. That malware is constantly monitoring the environment around the phone on which it is installed. Whenever an NFC capable credit card aka "contactless card" comes near enough to the infected phone to be detected (like when you shove it in your pocket with your wallet), the poisoned app sends a message over the internet to the attacker’s Android phone (the dishonest prover). The attacker then needs only to bring his phone near the NFC ready PoS machine and instantly, an illegal monetary transaction can be approved -- just as if you were standing there paying at that machine with your own device. The victim's phone doesn't have to be rooted or have any other special restictions, besides an unlocked screen, for the transaction to take place.
The security researchers successfully presented a live proof of concept demo on stage Thursday at HITB using a Nexus 5 as the dishonest prover and Sony Xperia S as the dishonest verifier. The researchers have also successfully tested the attack the Nexus 4, and Samsung Galaxy Nexus.
While the amount of money that could be stolen is restricted to small amounts ($50 or less) and only few transactions can be achieved before requiring a pin, the implications are still significant. There are currently some 300 mobile devices with NFC capability on the market today. According to a recent report by market research company Juniper Research Limited, there are expected to be some 500 million NFC payment users on the planet in 2019. Though there have not yet been any known cases of NFC relay attacks in the wild, with the large number of potentially exploitable devices, easy development of the malware, and fast revenue that can be obtained, Vila and Rodriguez believe it’s only a matter of time before “digital pick pocketing” with NFC relay attacks come into the spotlight.
How To Prevent NFC Attacks On Your Device

So how can users protect themselves from NFC attacks? Rodriguez shared this advice with iDigitalTimes: “Be aware of the apps you are installing on your device – don’t use apps that haven’t been approved in the Google Play store or that are from an alternative market. If you aren’t using NFC for other stuff, just deactivate it by default. That way the application must ask you to activate NFC and if an unauthorized usage, then you will know it.”
To learn more about Rodriguez and Vila’s research, see the full slides for their presentation here. Or read the technical whitepaper, here.
For More OSX, iOS, Jailbreak And Infosec News
Follow Cammy on Facebook, Twitter, or Google Plus
Send tips to c.harbison@idigitaltimes.com
GPG Key ID: 56E784D9







![Best Gaming Mouse For Gamers With Smaller Hands [2025]](https://d.player.one/en/full/227430/best-gaming-mouse-gamers-smaller-hands-2025.png?w=380&h=275&f=fdcf47c1c5fc58d1e41d3be505c12568)










