A new technique for de-anonymizing Tor hidden services traffic was revealed at Hack in the Box Security Conference in Amsterdam, Friday.
Researchers, Filippo Valsorda and George Tankersley demonstrated how attackers could potentially de-anonymize traffic of users accessing hidden services by utilizing a kind 'correlation attack.' The attacker would assume the position of the HSDir nodes for the hidden service allowing them to “see” exactly who has connected to a hidden service and when. The attack, according to Tankersley, is not only “really easy” to perform but also allows the attacker to de-anonymize traffic to “a specific hidden service at a very particular time.”
How Tor Works
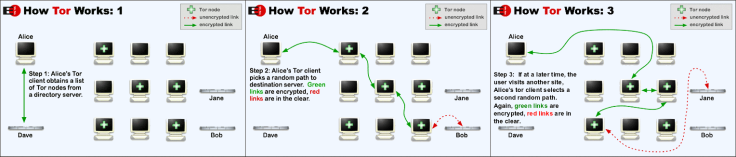
The Tor network is a free anonymizing software that allows for anonymous communication and web browsing by making it difficult for Internet activity to be traced back to the user. Tor works by building a circuit through other machines or relays. When you log into Tor, for example, to search something on the web, your client sends the request through a randomly selected set of relays. When the information gets to the end of the Tor network, your IP address remains hidden because it appears that your connection is coming from the IP address of a Tor exit relay. Every time you use Tor, the relays will be different making it impossible to figure out who is sending what request unless the attacker has the ability to match up the entry and exit nodes.
While there have been some successful attacks on Tor in the past, those attacks have been few and far between because of the many protections Tor has in place. Those protections make it a reliable way of keeping web activity anonymous.
In addition to regular Tor traffic, there are also things known as “hidden services.” These are websites found in the “deep web” and cannot be seen or found on the “regular” internet -- they can only be accessed by logging into Tor. While hidden services have become notorious for use in drug trafficking (i.e. Silk Road) they are also used to provide good services like SecureDrop, private chats, and anonymous publishing. Journalists, activists and other individuals who have a crucial need for hidden communication use these services.
Deanonymizing Hidden Services Through HDirs
Since deanonymizing traffic through the entry and exit nodes is so difficult, the researchers began to wonder if there was anything else that sees when a connection happens. The answer: hidden service databases.
When a person wants to host a hidden service, they have to advertise their service on a Tor Onion database, which is a DHT made up of a group of stable relay machines called HSDirs . The person who wants to visit the hidden service has to request information about that service from the database. Therefore, those relays or HSDirs can see who is making the request for a connection and when you want to connect. Therefore, to deanonymyze a user’s traffic, an attacker could choose to become the HSDir nodes for the hidden service.
“It’s actually very, very easy to do this,” Tankersley said. “To become the HSDir, all you need is four days of up time. It should be harder than it is, but it’s not."
“This is an open Tor bug,” Tankersley continued. “There’s a patch moving through the Tor Project to also require the 'stable' flag so this will get a little bit harder, but right now it’s very easy to become a specific HSDir for a particular hidden service at a very well known time. It’s predictable, fast and cheap to bruteforce the keys and become every HSDir for the hidden service.”
To demonstrate this fact, the researchers showed how they had managed to become all but one of the HSDirs for Facebook Thursday and the day of the presentation.
Such an easy attack vector could have serious implications for users who rely on the anonymizing hidden services Tor provides.
“Imagine a country where there is an activist movement that is not appreciated by the government,” said Valsorda, “and that government can see all the connections in the country through, say, an ISP. If they attack the HSDirs for some service that provides revolutionary information, for example, then they can tell for sure what homes connected to the service and when.”
Is There A Solution For Tor Hidden Services Bug?
While temporary mediation is in the works, Valsorda told iDigitalTimes that the bigger solution may be over a year away.
“Tor Developers are working on making it harder to become HSDirs, and on monitoring the network for suspicious activity,” Valsorda said “but these will only make the attacker require more resources. The real fix will come with the new generation Hidden Services. They are still being finalized at the proposal level, so the implementationhas yet to begin. Tor developers, however, have written that they plan to work on it during 2015 and 2016.”
At this point there is very little users can do to protect themselves from these HSDir attacks other than visit a site’s global or public web address. This way the user remains anonymous but lacks the traffic-encrypting feature.
On the side of the Hidden Service providers, the best solution currently is to become one’s own HSDirs. You can trust your own node so being your own HSDirs makes the most sense. This gives providers a form of detection as well. If they see other HSDir relays competing heavily for those positions, it could be a red flag.
To learn more about the research by Valsorda and Tankersley, see the full presentation materials here.
For More OSX, iOS, Jailbreak And Infosec News
Follow Cammy on Facebook, Twitter, or Google Plus
Send tips to c.harbison@idigitaltimes.com
GPG Key ID: 56E784D9


















