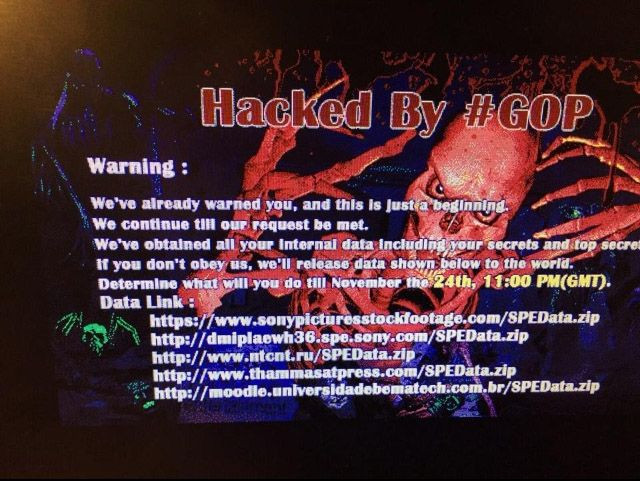
The Sony Pictures Hack has easily become the worst corporate hack of 2014 – indeed of all time – as several unreleased movies, executive salary information and the personal data of 47,000 employees was leaked across the internet last month. Over 40 GB of data has been leaked so far, while hackers responsible for the breech have claimed to hold 100 GB in all. The worst is yet to come, say the hackers, as employees and their families were threatened that danger could be ahead if they didn’t make their company ‘behave wisely’.
Since the November 24 hack, Sony Pictures has been working with the FBI and the Mandiant security firm to investigate who was behind the hack and begin the pick up the pieces from the wreckage, of which the breadth and width can hardly be quantified at this time.

In a Friday memo to Sony employees, Mandiant’s head of security, Kevin Mandia, wrote that the attack on Sony was “unprecedented,” and that the malware used was “undetectable by industry standard antivirus software.”
“The scope of this attack differs from any we have responded to in the past”, wrote Mandia, “as its purpose was to both destroy property and release confidential information to the public. The bottom line is that this was an unparalleled and well-planned crime, carried out by an organized group, for which neither SPE nor other companies could have been fully prepared.”
Mandiant’s assertions that the hack was unforeseeable seemingly worked to absolve the Sony Corporation from responsibility for the breech and were soon met with heavy criticism in the security community.
“Mandiant saying that nothing could have prepared Sony is like saying that patching is the only defense against 0days.” -- @addelindh December 8, 2014
"TIL Mandiant sells indulgences." -- @thegrugq December 8, 2014
"Unprecedented in nature" is also a wonderfully ambiguous turn of phrase that could have come from a medieval pope's playbook” -- @botnethorror December 8, 2014
"Anything to absolve the sin of 'likely insider threat via gross negligence'— Sony even chose which clerisy by lesser venial sin…” -- @z31r4m December 8, 2014
“Obviously they are trying to save face and go for the ‘we couldnt have helped it’ angle. Lame, stupid and obviously not true.” -- @Ar0xA December 9, 2014
In speaking with Andreas Lindh, a security analyst working for iSecure Sweden, he had this to say about Mandiant’s response:
“Saying that nothing could have prepared Sony for what happened is ignoring a large part of the chain of events. While I agree that the destruction of data and posting of stolen information online is not what typically happens after a breach like this, that was still preceded by the initial intrusion and the gathering and exfiltration of stolen data, all of which could have been detected and dealt with. Some sources have claimed that the attackers were in Sony's networks for up to a year, and that's a lot of time to detect an intruder, and especially one that's uploading terabytes of data. This makes Kevin Mandia's statement sound very strange to me, as it's basically like saying ‘there's no point in trying to defend yourself.’
Mandiant is a company with some extremely talented people on staff and Kevin Mandia himself knows what he's doing, so him saying something like that sounds a lot like he's trying to save Sony's face, and possibly to secure some future revenue by telling Sony what they want to hear.”
And, indeed, in details uncovered by Fusion, it became clear that the securing the sensitive data and information of employees was hardly a priority for the Sony Pictures Corporation.
“Sony’s ‘information security’ team is a complete joke,” one former employee told Fusion. “We’d report security violations to them and our repeated reports were ignored. For example, one of our Central European website managers hired a company to run a contest, put it up on the TV network’s website and was collecting personally identifying information without encrypting it. A hack of our file server about a year ago turned out to be another employee in Europe who left himself logged into the network (and our file server) in a cafe.”
Fusion’s report also revealed that the security team at Sony was relatively small – 11 in all. Meanwhile, another employee revealed that when risk assessments were completed and vulnerabilities were discovered, advice for fixing the issues was rarely heeded.
“The real problem lies in the fact that there was no real investment in or real understanding of what information security is,” another former employee told Fusion.
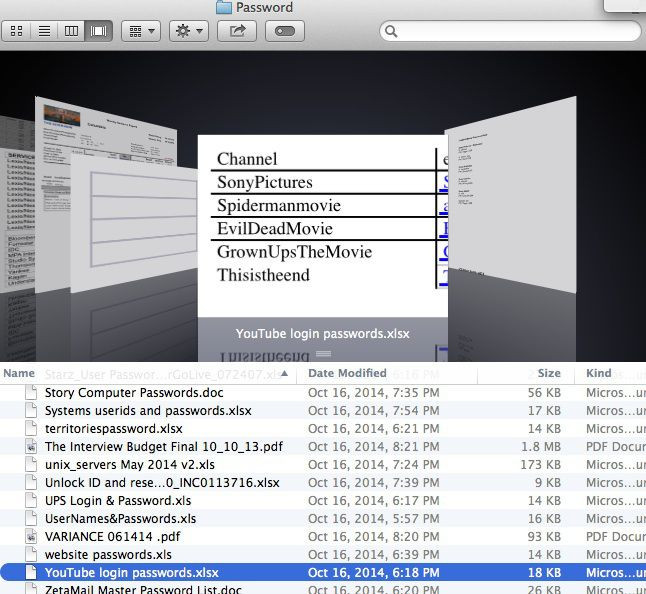
This fact became clearer still, as further investigation into the hack revealed that sensitive files on the Sony Pictures network were not encrypted internally or password-protected. In fact, a folder, which contained a comprehensive listing of social media and other usernames and passwords for Sony Pictures, was being stored in plaintext, in a folder labeled “Passwords.”
In a 2007 CIO interview with Jason Spaltro, Sony’s head security officer, we see a glimpse into the company’s attitude concerning security. In the interview Spaltro asserted that it was a valid business decision to accept the risk” of a security breach, and that he wouldn’t invest $10 million to avoid a possible $1 million loss.
“We’re trying to remain profitable for our shareholders, and we literally could go broke trying to cover for everything. So, you make riskbased decisions: What’re the most important things that are absolutely required by law?”
But the recent Sony hack has made it crystal clear that minimum compliance can no longer be an acceptable attitude among teams responsible for securing the sensitive details of a company and its employees.
In an in-depth assessment of the situation, the security research team at Thinkst made a pointed case for more preventative measure to be taken by companies across the globe as the Sony hack is only the beginning of a new age of insider information attacks.
“For a long time companies have gotten away with lax security because attacks translated to DDoS or defacements. While these certainly had some impact, most companies figured out how to deal with DDoS a decade and a half ago … In some ways, this has filled security teams the world over with a type of complacency: Even if things went perfectly wrong, they were ok. But things have changed …
The combination of WikiLeaks and Snowden revelations worked in concert to make potential attackers more aware of the benefits of hacking. Attackers who were historically technically focused, tended to focus on technical compromises … this changed dramatically when faced with knowledgeable insiders gone rogue, or informed outside attackers focused on well-chosen goals.
It doesn't matter whether or not the Sony attackers achieved root privileges on the local file-server, since they were able to get read-access to the data store holding upcoming movies. It doesn't matter if the attackers were able to get remote code-execution on the HR system, as they were able to get ahold of memos that showed the inequities of staff salaries. It doesn't matter if the attackers obtained domain administrator privileges on the internal network, as they were able to grab passports and social security numbers of high profile celebrities.”
To that the researchers added,
“We believe that more and more attackers will focus less on technical wizardry and more on real world results. We believe that these attacks, in many cases will require less work, but will have disproportionately large results … breaches like Sony are a shining beacon leading to the inescapable conclusion that an appetite for risk cannot be determined in vacuum without considering all the assets being protected.”
In closing, the Thinkst team made a plea for companies around the globe to reconsider the value of security and the people they are hiring to secure them.
“A common theme over the past few years has been to chastise ‘technical-geeks’ for failing to consider business needs while falling back to ‘risk-based calculations’. It is our belief that while risk-based calculations make total sense, in many cases these risks are impossible to quantify without a deep understanding of the technical possibilities too. People who understand both sides of this deeply are unicorns that need to be sought out and used.
The drama is far from over, and we are sure that more information will come to light … Sony Pictures has been comprehensively compromised, and recovering from this attack will cost millions of dollars and many man hours. Although we have seen lots of compromises in the past, this attack was different as it combined technical destruction with deliberate tactical “leaking” and asset theft. We believe that these sorts of attacks will only increase in frequency, and suspect that many organizations are far from ready for them. We believe that a good deal of rethinking is necessary to re-aim corporate security efforts to handle these sorts of attacks.”
To read the entire report by the Thinkst team, visit their blog at http://blog.thinkst.com/2014/12/yabotsb-yet-another-blog-on-sony-breach.html


















