From the day the first iPhone released, it has garnered the attention of hacker hobbyists and security researchers across the globe. Beginning with George Hotz's (Geohot) debut hack that unlocked an AT&T iPhone for use on the T-Mobile network, and continuing through the most recent evasi0n iOS 7 jailbreak, interest in pushing the envelope on Apple's user restrictions has grown exponentially. While with each new version of iOS firmware that releases new security challenges appear, those challenges are met with the enthusiastic interest of iOS researchers near and far. And with each new public jailbreak that is released, a growing level of consumer interest is incited as well.
Those who have watched the development of the information security field over the last several years have seen the increasing level of attention mobile security is receiving in the news. It's not unexpected then, that many would be interested in learning to break these systems or secure them. But how does one begin? How does one learn the skills necessary to become a security researcher? Where can one get the information needed to begin understanding how Apple's iOS works and test it for weaknesses?
Damn Vulnerable iOS App: A Damn Vulnerable Application For N00bs, App Developers And More.
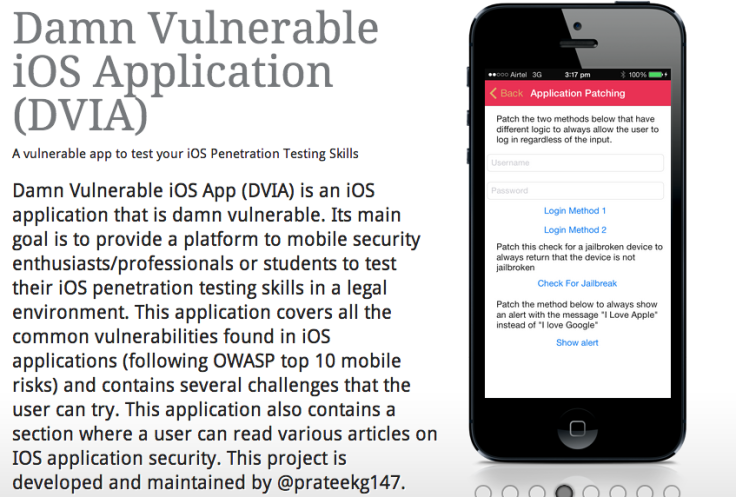
For those who are just getting their feet wet in iOS security research or for app developers who want to learn good and bad practices in app writing, there is a new free open source tool available for iOS penetration testing practice along with some valuable resources to accompany it. The tool is Prateek Gianchandani's "Damn Vulnerable IOS App (DVIA)." DVIA is a platform for mobile security enthusiasts, professionals or students to test their iOS pen-testing skills in a legal environment.
The application offers users a vulnerable platform in which to learn about and test many common vulnerabilities found in iOS applications. In addition to the app itself, the author has published a series of tutorials for those who want to learn iOS Application pen-testing — regardless of experience level. While this app is geared mainly towards beginner and intermediate level hobbyists or professionals, plans for a pro version of the app are underway, However, for the n00bs here is what DVIA offers.
"My tutorial series starts right from the basics, which is jailbreaking an iOS device and setting up a mobile penetration-testing platform. It then moves on to explain the fundamental issues with the iOS platform and the common vulnerabilities that exist in iOS applications. After that, it dives into some advanced stuff like using automated tools, reverse engineering and patching iOS applications. All you need is an iOS device to get started with it and then you can move up through the tutorials one by one. A little bit of knowledge in working with terminal commands will be a good advantage but I have written this series keeping beginner's in mind," Gianchandani shared with iDigitalTimes.
So You Want To Make A Jailbreak? DVIA May Be A Good Starting Place
The resource available will be attractive to those who want to quickly start playing with vulnerabilities. In a few minutes, you can download this app, and start to interact with it and see how it crashes. In some ways, the app mirrors a Capture The Flag activity or CTF. According to Gianchandani, CTF served as a basis for the app conceptually, but it has been modified to accommodate beginners.
"I have created CTF applications for contests before and initially thought about creating a CTF style application but decided that it will only be useful for a handful of people as CTF is not that a good way to start for beginners. I wanted to create something that would target a much wider audience and something that people can actually learn from. So I thought of creating DVIA. I do have plans to create CTF like apps in the future though."
For those who are interested in moving down a path toward jailbreak development, this app and the associated tutorials offer great value. DVIA has multiple challenges to overcome — a popular one being how to stop app jailbreak detection.
"Many developers add a check in their application to detect whether the device is jailbroken or not and only permit the app to function properly if the device is not jailbroken. Similarly, this application has a check to detect a jailbroken device. The user's task is to bypass this check and fool the application into thinking that the device is not jailbroken using their hacking skills," said Gianchandani.
How DVIA Can Benefit iOS App Developers
The DVIA app however, isn't just for beginners or those aspiring to create jailbreaks. The resources presented can be quite valuable for those who are active in iOS app development as well.
"Enterprises are rapidly moving towards the mobile platform and every popular business wants to have a space in the mobile domain. We carry so much private information on our mobile phones. Every now and then some vulnerability is discovered in a popular mobile application that poses a risk to the user's privacy. It is quite clear that most of the mobile developers don't understand the risks associated with an insecure mobile application and the measures that should be taken to avoid it. This application is specifically aimed at teaching developers the fundamental skills associated with building a secure mobile application though various challenges."
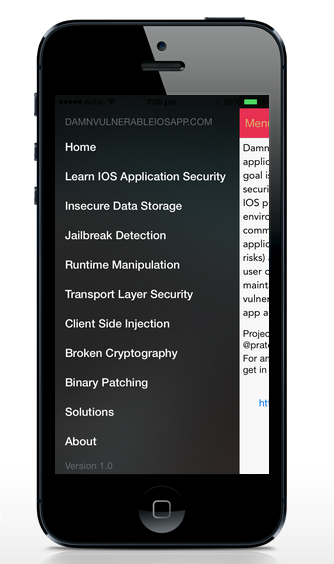
Some of the challenges DVIA offers include,
a) Insecure Data Storage
b) Runtime Manipulation
c) Transport Layer Security
d) Client Side Injection
e) Information Disclosure
f) Broken Cryptography
g) Application Patching
What iOS Security Researchers Are Saying About DVIA
Upon reviewing the DVIA and the information Gianchandani's tutorials provide, hardware engineer and iOS jailbreak creator @MuscleNerd agreed they were valuable indeed.
"I mean, he's got loads of information on the site. Just that is valuable, even if there weren't an app too ... this is a really neat effort he's got going ... to put forth that much for free is awesome."
To that forensic scientist and author of "Hacking and Securing iOS Applications" (A book designed to help developers both hack and write secure apps) Jonathan Zdziarski added,
"Providing a free app that's designed with flaws so students can learn to pen test is not only really cool, but should really help many of the developers out there struggling to write secure applications for iOS. Most of the banking apps, password apps, and other apps protecting our personal data in the App Store today are written very poorly; this should help to up the ante."
Why DVIA? Prateek Gianchandani Discusses Motivation And Future Plans
When asked what his motivation was for developing DVIA, Gianchandani told iDigtialTimes,
"Three years back, when I began developing iOS applications, I realized that there was so much out of the box stuff that can be done with an IOS device. So I jailbroke my device and everything started from there. As I dived more into iOS development, I realized that there was very less awareness among iOS developers on how to build secure mobile applications. Also, the trend in the security community was changing. As smartphone usage was growing exponentially, it was also becoming a more preferred target of attack for hackers.
I had previously used an application named Damn Vulnerable Web application that taught users the basics of Web Application Security through a web application deliberately made insecure with challenges that the user can try. I learned a lot from it, so I thought that I could give something back to the community and make something like this for the iOS platform ... therefore, I have written a complete series of tutorials on iOS Application Security. I thought that these set of tutorials could be a good addendum to the application."
Gianchandan has been involved in Web Application Security and Penetration testing, for 7 years now, but he has focused more specifically on iOS in the last three years.
"Security is my passion", said Gianchandan. "it's what I live for. Not to mention, I am also a diehard Apple fanboy and willing to argue with anyone who thinks Android is better."
DVIA's Future: Will The Vulnerable App Be Allowed On The Official Apple App Store?
Gianchandan has successfully submitted a number of apps to the Apple app store in the past, and his hope is to have the DVIA app accepted as well. However, getting the app accepted may not be so easy. Gianchandan currently offers DVIA as an open source application available at https://github.com/prateek147/DVIA. Speaking with QuarksLab security researcher and creator of the evasi0n 7 jailbreak, Cyril Cattiaux (@pod2g),he voiced concern over whether DVIA could successfully be added to the Apple app store.
"This guy is basically submitting a vulnerable application to the AppStore with its source code. Which means that it could be an entry point for unsigned code exec, and who knows, a jailbreak maybe? Would Apple accept such a thing?"
But either way, Gianchandan intends to try.
"This is definitely on the cards. I might have to strip off some stuff from the app to get it approved from Apple though. Stay tuned! "
In addition to trying to get DVIA on the Official Apple app store, the security researcher shares that updates and additional resources are in the works as well.
"More features, more challenges, more tutorials and a bit of redesign in the app or coming. I am also thinking of building a different CTF like app for the pros. And yes, I want to make the solutions free. I welcome any suggestion from the community on what they want to see in the future versions. "
To contact Prateek Gianchandani about his work or just to say hello, you can find him on Twitter as @prateekg147. You can also send an email to prateek@damnvulnerableiosapp.com and he assures me he will respond.

Cammy Harbison
Writer/Reporter For iDigitalTimes
For More OSX, iOS, Jailbreak or Infosec News
Follow Cammy on Facebook, Twitter, or Google Plus