Zepto, Bart and CryptXXX are among several new types of ransomware attacks cropping up during the month of June. Find out how each of these ransomware attacks are spreading and how to protect yourself from infection.
Ransomware is the fastest growing and most lucrative form of malware, cyber criminals can leverage today, leading to an escalating upswing in new ransomware development each month. In the last six months, ransomware infections have increased a startling 44 percent taking victim countless millions. From personal computers to massive health care organization networks, the attacks are hitting all types of users. In the last month alone, we’ve seen a variety of new developments in ransomware from new releases to unique vectors by which cyber criminals are leveraging their attacks. We at iDigitalTimes have done an extensive amount of coverage on the topic of ransomware and with the speed at which this form of malware is growing and changing, we’ve decided to begin a monthly Ransomware Update report post to let you know the new and developing threats actively taking victims captive.
In this month’s edition, we have four different manifestations of ransomware to discuss – some of which have only come to light in the last few hours or days. In this report, we discuss the names of the ransomware and, where known, the methods by which they are infecting users. We also include information on how you can protect yourself from infection.
#1 Zepto Virus – Locky Ransomware Gets A New Name
DESCRIPTION:
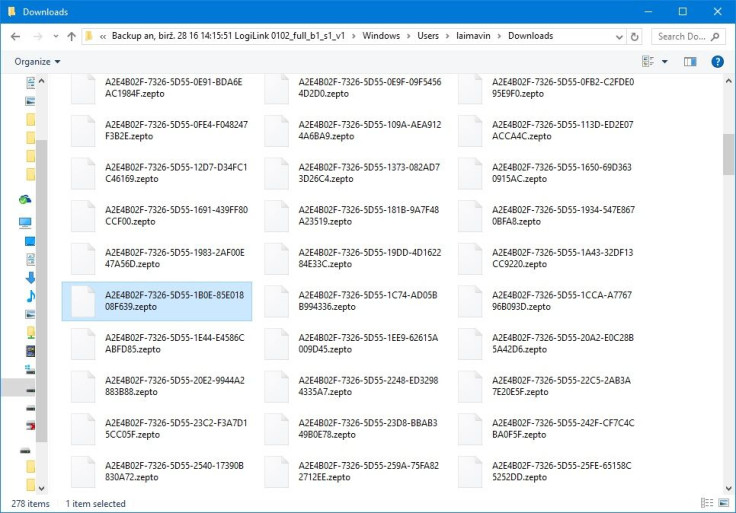
Zepto is the very latest version of ransomware to strike internet users and thus far, there’s not a lot of information on the virus or how users are becoming infected. According to Bleeping Computer, the Zepto ransomware appears to be a version of Locky ransomware that is now changing the file name of encrypted files to .zepto.
Researchers at Symantec had recently reported Locky infections were down in first few weeks of June. It appears with Zepto, however, they may be making a comeback.
ZEPTO RANSOMWARE DECRYPTION TOOLS:
Zepto ransomware is very new but as it is a form of Locky ransomware, there is currently no way of decrypting files encrypted. Your only option for recovering the files is to have a back-up available or pay the ransom. Users are never advised to pay ransom to cyber criminals.
Because of the newness of Zepto, some anti-virus, and anti-malware programs may not be detecting it yet. As more is learned about the Zepto virus infection, we’ll be sure to provide updates.
#2 CryptXXX – An Oldie Gets Revived
DESCRIPTION:
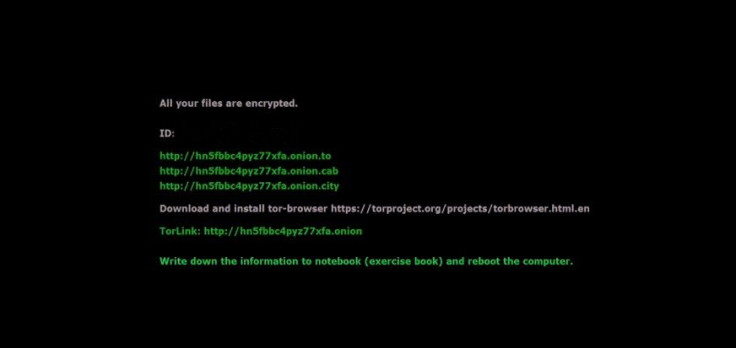
CryptXXX had been relatively inactive for a while, but during the month of June, it began making a comeback. According to Sentinel One security team, the newest version of CryptXXX ransomware has fixed flaws in its file encryption methods, rendering the previously available decryption tools useless.
CryptXXX is a downright nasty form of ransomware, which not only encrypts files on a victims’ computer but also attacks any files on connected storage devices. The ransomware can also steal cryptocurrency wallet funds stored on your system or send sensitive data to cyber attackers for further hacking.
According to Sentinel One, CryptXXX gathered about $50,000 worth of ransoms money in Bitcoin between June 4 and 21st and will likely continue to actively attack users across the globe.
CRYPTXXX DECRYPTION TOOLS:
At this time there is no way of decrypting CryptXXX. It is believed that the ransomware is largely spreading via spam. Users should take caution with opening emails and particularly email attachments from parties that are unknown. For more information on avoiding phishing and spam attacks, check out Panda Security’s official blog post on preventing phishing attacks. In addition, Malwarebytes has an excellent post on preventing ransomware infections.
#3 Bart Ransomware
DESCRIPTION:
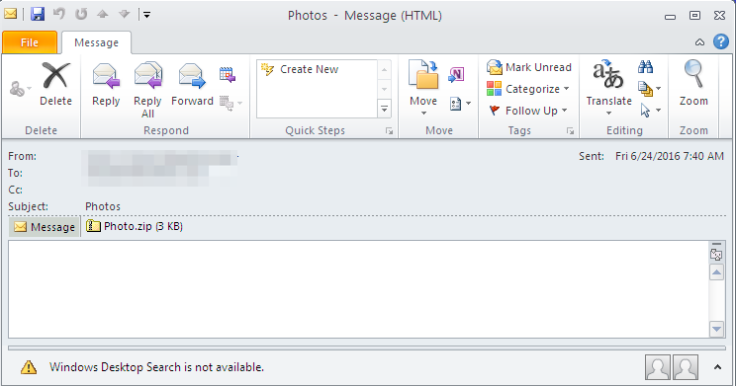
Bart Ransomware cropped up around June 24 as researchers at Phish Me discovered the new file stealing malware was being distributed via phishing emails titled “Photos” with an attached zip file that is presumed to be photos an acquaintance is sending to the user. When the infected zip folder is opened, it contains javascript files for a malicious program called RocketLoader, which is responsible for installing Bart ransomware on computers.
Once infected, users receive a ransom message similar to the one distributed by Locky developers. Incidentally, ProofPoint researchers believe the creators of Locky are also behind Bart ransomware. Bart is a more efficient way of encrypting files than some ransomware as it doesn’t communicate with a Command & Control server. This means it can continue to its dirty work even if the computer isn’t connected to a network. Bart is also interesting in that, it doesn’t encrypt individual files. Instead, it sends them to a password protected zip-file archive that remains locked up until the ransom is paid.
BART RANSOMWARE DECRYPTION TOOLS:
At this time there is no way of decrypting or unlocking files secured by Bart. It is believed that the ransomware is largely spreading via phishing emails labeled “Photos.” Users should take caution with opening emails and particularly email attachments from parties that are unknown. For more information on avoiding phishing and spam attacks, check out Panda Security’s official blog post on preventing phishing attacks. In addition, Malwarebytes has an excellent post on preventing ransomware infections.
#4 – Cerber Ransomware – Office 365 Users Become Latest Victims
DESCRIPTION:
Cerber Ransomware began rearing its ugly head in earlier this year as a number of users became infected via spam messages or poison ad campaigns leveraging a vulnerability in Adobe Flash Player. Since it first arrived on the scene Cerber has been heavily traded on the Russian underground market. The ransomware is unique in that it includes an audio message for users who are infected.
The most recent Cerber ransomware attacks have also come via phishing but targeted According to researchers at Avanan on June 24, a massive number their customers who used Office 365 email were sent at least one phishing email that contained an infected attachment which installs Cerber ransomware. From its research, Avanan believes an estimated 57 percent of all Office 365 mail users were likely sent the same infected email. At the time of the attack, Office 365’s built-in security tools were not able to detect the Cerber virus inside the attachment. It took about a day before Microsoft’s detection systems began blocking the infected emails. It is unknown how many users may have been infected by the email.
CERBER RANSOMWARE DECRYPTION TOOLS:
At this time there is no way of decrypting or unlocking files secured by Cerber ransomware. It is believed that the ransomware is largely spreading via phishing emails. Recently, Office 365 mail users were targeted specifically. Users should take caution with opening emails and particularly email attachments from parties that are unknown. For more information on avoiding phishing and spam attacks, check out Panda Security’s official blog post on preventing phishing attacks. In addition, Malwarebytes has an excellent post on preventing ransomware infections.


















