A recent Myspace hack database of 360 million user accounts marks the largest password leak in history, but “Have I Been Pwned” creator Troy Hunt believes larger breaches may be on the way. Find out about the connection between the recent Myspace, LinkedIn, Tumblr and Fling hacks here.
On Tuesday, Myspace confirmed reports that a database containing 360 million breached accounts was being sold on the dark web for 6 bitcoin – about $2,800 at the time of the post. If all the accounts in the database turn out to be unique and authentic – and according to researchers analyzing the breach, they likely will be – it will mark the largest password leak we’ve ever seen.
But the leak comes as only one the latest in a string of prominent account breaches that have making the news in the last month.
The trend began in early May when reports that account login and password information for 40 million Fling.com users were being sold on the Dark Web appeared in the news. A week later, Yahoo announced a third party had gained access to an unconfirmed number of Tumblr accounts. The company later revealed the account breaches totaled some 65 million user accounts. On the heels of the Tumblr hack came the LinkedIn hack, which included login credentials for some 167 million accounts.
According to Troy Hunt, creator of the free website Have I Been Pwned, which is dedicated to informing victims of data breaches, the four May account breaches fall in the top 5 out of 109 largest password leaks he’s recorded to date.
While this string of breach is daunting, according to Hunt, we may be in for even bigger surprises in the near future.
“There are rumors among those who travel in these circles that there is more data yet to come even bigger than what we’ve seen so far,” Hunt told iDigitalTimes.
But why the sudden upturn in account breaches? While all the pieces of the puzzle have yet to come together, there are interesting patterns in each of the breaches that can give clues to what may be ahead.
Each Breach Involves Old Data
The first correlation between the four hacks is that they are all comprised of data from 2013 or earlier. According to Hunt, the Myspace data may be from as far back as 2009 .
“Nothing much has changed at Myspace since 2008, which is quite a few years,” said Hunt, “so their data from eight years ago might look very similar to the data today.”
Regardless of the exact age, each of these breaches are pretty old, channeling a time when account security measures were not as strong as today.
The fact the breaches are old is proving particularly taxing for companies like Yahoo or Time Inc who acquired the likes of Tumblr and Myspace, respectively, after the date of the data breaches.
In the case of Tumblr, a Yahoo representative told iDigitalTimes “the breached data is three years old [from before Yahoo purchased Tumblr], so we don’t have forensic information from that time.”
Meanwhile, Hunt reported that in the case of the LinkedIn breach, there were oddities in how users were notified. From his analysis, it appeared the company may have sent password reset emails to any address on the leaked lists – whether they were actual LinkedIn users or not, suggesting that the company may not have adequate data to investigate the breach.
The age of the breaches is causing problems for users as well. Myspace or Tumblr users, for example, who have let their accounts lie dormant for several years, may have used an email address they no longer have access to. This makes it impossible to change a forgotten password, delete an account or determine if they may have reused the password elsewhere.
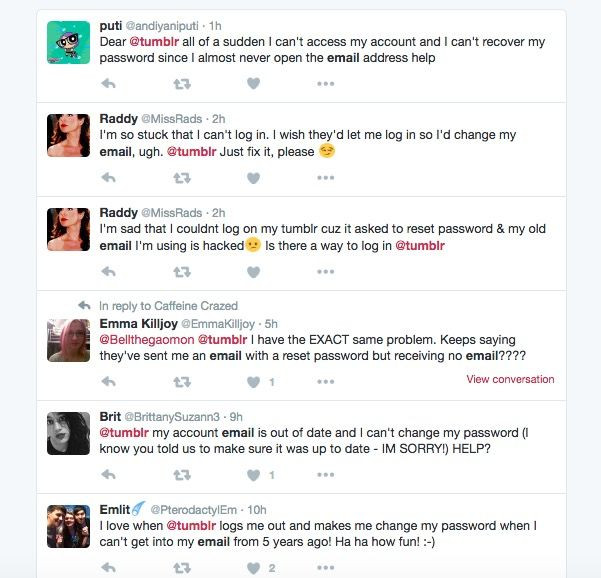
All The Breaches Were Leaked By The Same Hacker
The second connection between these breaches is that they were all leaked by the same hacker on the same forum.
“We started to see data emerge from this fellow called Peace_of_Mind on The Real Deal” Hunt said.
The Real Deal is a dark market site, on the Dark Web, which means users cannot access via a regular web browser. They must use the Tor Onion browser. While the site allows people to post a variety of illicit materials for sale such as software vulnerabilities, hacks and prescription drugs, it’s not especially difficult to access.
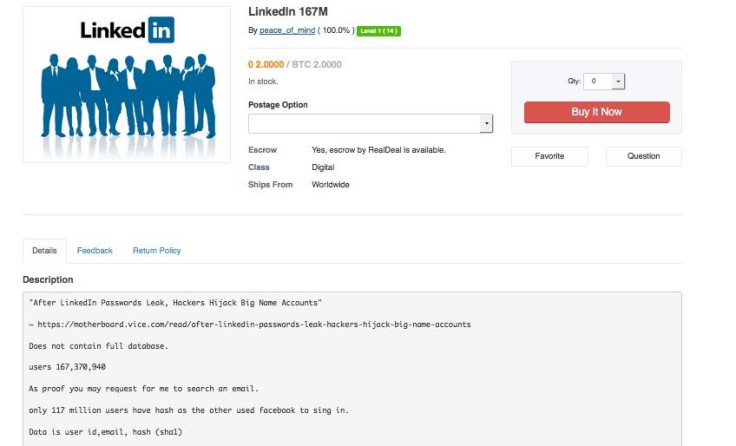
Hunt reported seeing Peace’s advertisement for the Fling, Tumblr, LinkedIn and Myspace data all posted on the site at various times for 5-6 bitcoin. At the time of this writing, the LinkedIn breach is still being sold by Peace for 6 bitcoin.
The Breaches Are All Separate And Authentic Incidences
Unlike the “massive email hack” reported by Reuters in early May, which turned out to be a lot of compiled junk, these four hacks have each proved to be individual and authentic.
“They aren’t fake, fabricated or coupled together from other data sources,” said Hunt. “I’ve done my own verification and there’s no doubt these are authentic. There also haven’t been any rebuttals from the affected organizations saying it’s not accurate and we certainly often see that.”
Those who paid to acquire the hack databases gained access to victims’ usernames, email addresses and one or two different passwords, which may have been reused across countless, web accounts.
Although each of these hacks have all been offered by the same hacker, it’s unknown if he is the originator of the hacks. While Hunt acknowledges Peace may have been behind them all, there are clues that suggest he may have acquired them from other sources.
“We could reasonably speculate that he did hack the systems himself,” said Hunt, “but one thing that is telling is that these incidents happened quite far apart – over a three-year span or more. It’s not like he went on a bender where he had a zero day in a particular framework that allowed him to exploit everything in a short period of time before it was patched. These breaches are much more spread out than that.”
Whether Peace breached the systems himself or acquired them from other parties, one thing is sure: he’s reliable.
“Peace has a very good reputation on this Real Deal site,” said Hunt. “The feedback from buyers shows they are all very satisfied so he’s clearly is delivering.”
As we learn more about the details of the recent breaches or what may be ahead, we’ll be sure to provide updates.


















