On Friday a serious security issue— the SSL Bug — arose in the Apple iOS/OSX community, which should be alarming to anyone using an iPhone, iPad, iPod or Mac computer. While there is a solution available for those on iOS devices, Mac computer users are still highly vulnerable to attacks which could allow all their sensitive data — passwords, text messages, credit card and banking information, emails, Twitter and Facebook access and more — to be retrieved and controlled by hackers with even low level skills. In this post I will explain what users should do to protect themselves as well as what happened with Apple's SSL/TLS protocol because of the "goto fail;" issue. I would encourage anyone — no matter how low your interest or expertise in computers — to read this article in its entirety. It will offer valuable education and understanding of how information security issues affect you personally.
Who Is Vulnerable To The Apple SSL Bug?
The Apple SSL bug affects all Apple computer users and nearly all iOS device users. Whether you have an iPhone 3GS running 6.1.3 or a MacBook Pro on the latest version of OSX Mavericks, you are at risk for data breach right now if your device has not been patched.
What iOS iPhone, iPad, iPod And Mac Computer Users Should Do To Protect Their Security Due To The SSL Bug
On Friday, Apple pushed an update to iOS 6.xand 7.x to patch a serious issue discovered in Apple's SSL/TLS browser software. Simply updating your iPhone, iPad or iPod to the latest version of iOS — iOS 7.0.6 — will patch the problem. For iOS 7 jailbreak users who are concerned about losing their jailbreak, fortunately this fix does not patch the jailbreak. After updating, the latest version of evasi0n iOS 7.0.6 jailbreak can be found at evasi0n.com. At this time, however, there is no fix for Mac computer users. As such, there are steps that users should take to keep themselves safe until Apple pushes a fix. According to Apple spokesperson, Trudy Miller, that fix should become available "very soon."
If you are running a Macintosh computer, do not connect to any public Wi-Fi locations at all (Ex: Starbucks, pubic library etc). By doing this, you put yourself at high risk of being hacked. If you are using a home or work internet connection, make sure that the connection is secured by a password, otherwise, the same risks apply. Once Apple does release the update for Mac OSX, update immediately.
(UPDATE: Apple has released an update to OSX. To patch your Mac computer or laptop, download the latest Apple OSX software via the Apple App Store)
What Happened With Apple's TLS/SSL? Why Is It So Important To Patch?
Despite the fact that a fix is available for iOS devices, many people have been reluctant to do it as they are unsure of the importance — particularly users within the jailbreak community. Some complain of the free memory required for the update, or the need to perform a back up, or how long the update may itself take to perform. I mean, what's the big deal? After all, aren't we reading about some security breach or other every day in the news?
This particular issue, however, is probably worse than any major flaw in computer software than we've seen in a long time, and has the potential to expose the sensitive data of countless Apple users who remain unpatched and unaware.
RELATED: iOS 7 Jailbreak SSL Patch: Ryan Petrich Offers 7.0.6 Security Fix Without Needing To Re-Jailbreak
How TSL/SSL Works
The SSL bug has everything to do with the fundamental way Apple encrypts data. As users of the Internet, we are constantly sending and receiving data on our mobile and other Internet connected devices. The only way we have any semblance of security, is in the knowledge that SSL/TLS protocols (guidelines or digital rules that have been set up for how data is exchanged within or between computers) are in place, which protect the sensitive data that we are sending. The data I am referring to can be anything from the emails you send in your workplace, to the texts you send to your spouse, to the credit card information stored in your Apple ID, your PayPal account, etc.
With a healthy and functioning TLS/SSL, sensitive data can be, for the most part, transmitted securely without risk of being exposed to unauthorized individuals/entities. However, if a flaw is discovered in the TLS/SSL, then the potential for all of your sensitive data to be transmitted to a random, and in many cases, nefarious third parties is exceptionally high.
Here's why:
The job of TLS/SSL is to encrypt data we send and receive in such a way that only authorized parties can read it. Encryption doesn't prevent hacking, but it reduces the likelihood that the hacker will be able to read the data that is encrypted.
In addition to encrypting data, TLS/SSL follows a long series of protocols to ensure that who you are sending your data to is actually who they say they are, and who you are receiving data from is also who they say they are. How is this accomplished? There are numerous steps.
Here's a rundown of what happens, for example, when you type www.google.com into your browser.
1) Your browser makes a secure connection to a website (google.com)
2) The site you are trying to visit presents your browser with a certificate chain (this is what tells your browser the site is who it says it is — like a license or photo ID)
3) Your browser will then check the site's certificate to make sure that it matches the site you want to connect to — google.com (It's like when the police look up your license number and registration in their computer when you get pulled over).
4) Since the only website that has the real "google.com" certificate is Google.com, then no other site can present that certificate — or if they do, it'll soon become obvious the site and the certificate don't match (To draw on my analogy further, it would be like handing a cop someone else's ID. He's gonna look at you and know it isn't right). If your browser sees the certificate they've been given is not for google.com, then it will refuse to connect.
5) In addition to verifying the certificate, your browser will also verify that a trusted certificate authority issued the certificate. In other words, though you or I could create a phony driver's license that might fool some, when the police check it in the computer system, they will soon know if that ID is actually valid and has been issued by the county, state or province listed on the ID. In the same way, attackers can generate fake certificates for google.com, but since that attacker does not have a trusted certificate, it won't be accepted by the browser as genuine.
6) But these are not the only steps a TLS/SSL takes to ensure the authenticity of the source to which you are about to give your information. The browser will also verify the certificate chain's signature with the website's public key. The key that an attacker uses to make that fake certificate won't match Google.com's public key. This would be similar to checking your fingerprint against the one associated with your driver's license.
How Did The SSL Bug Happen? Where Apple's SSL Failed
So how did Apple's SSL fail so miserably? Even if you are not a coder, I'm fairly certain you can understand this one, once explained. To begin, here s a snippet from Apple's published open source code.
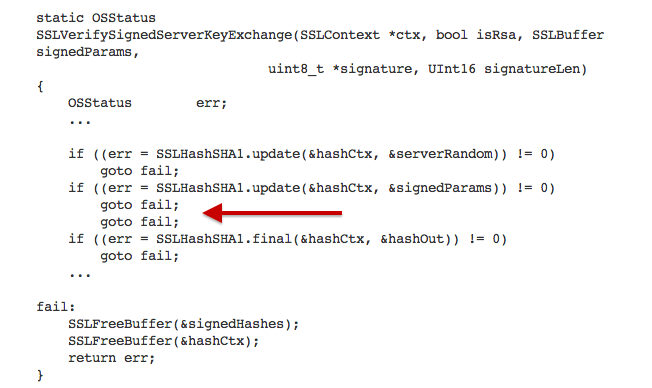
This code is part of the long chain of steps I just explained above that the TLS/SSL goes through to ensure the website you are going to transmit information to is actually who they say they are. If you look at the snippet of code, you'll notice a repeated line: "goto fail;"
What this line basically tells the computer, is, if an error occurs in checking the authenticity of the website you want to visit, then it is a fail, and you won't be sent to that website.
As the computer goes through this series of steps, as long as each one "checks out," it continues to move down the line. If they all check out, then the website is displayed.
Where the problem comes in here is that there are two "goto fail;" statements in a row.
The second one, as you can see, comes just before the last bit of code is run in that series of verification steps. That last step would have been to validate the certificate's signature. However, because of the second "goto fail;" the computer hits the first one and it checks out. When it hits the second one, the computer thinks its work is done, having stored the last value it checked — the value from step 5 — which was completely valid. This means it never does actually get to that step of validating the certificate signature (i.e. fingerprint) — step 6. So basically, unbeknownst to us all, every website that made it through all the checks but the last one were let through.
If Apple's SSL Bug Has Been Around A While, Why Such A Fuss About It Now?
Now, up to this point, no one was aware of this error, as it was not reported by a private security researcher, but appears to have been discovered in house at Apple. The problem is, Apple's SSL bug has now become so visible in the media and so thoroughly explained, that even a low level hackers with little proficiency could get access to all your private information as long as you remain unpatched and using a public Wi-Fi network.
The implications here are quite grave. Basically, for users running iOS 7.0.5 or below, anytime you connect to a public Wi-Fi network, be it at Starbucks or the library, or even at your home or office if it is not password protected, you put yourself at risk of having all your personal and sensitive data stolen, including bank account information, text messages, emails, Facebook, Twitter — everything.
As a result of this massively unfortunate fail, it cannot be stressed enough how important it is to update you iOS device to 7.0.6 immediately.
For those who are using a Mac computer — which runs OSX — at this time there is actually no patch at all. It is therefore paramount to your security that you do not use any public Wi-Fi networks to browse the Internet via Safari. In fact, some security experts feel so paranoid they are recommending not browsing period. According to QuarksLab security researcher and iOS jailbreak creator Cyril Cattiaux, aka @pod2g,
"Mac does a lot of things in the background, like requesting your emails, connecting to iCloud, the AppStore etc. Therefore, an attacker could also forge a false update server, probably allowing remote code execution."
In short, even if you use a different browser than Safari — like Google Chrome or Firefox — you are still at risk of being hacked if you are on a public or unsecured network.Users on public networks, however, aren't the only ones at risk. When discussing the issue with Nick Arnott at iMore,
"An attacker who is able to get on a network anywhere between you and the destination server can exploit this. Case in point, people are wondering if this is how the NSA undermined Apple's SSL. Until this is patched in OS X, any connection you make — whether you are in at home, on Wi-Fi somewhere, plugged in at work — any connection made by an app using SecureTransport is at risk. For example, technically, the attacker could be some shady dude at your ISP doing a MITM. It doesn't have to be an unknown hacker. "
If you have any further questions about the SSL bug and the security of your device, feel free to leave a comment and I will do my best to answer them.
Cammy Harbison
Writer/Reporter For iDigitalTimes
For More OSX, iOS, Jailbreak And Infosec News
Follow Cammy on Facebook, Twitter, or Google Plus
Other Pieces By Cammy Harbison


















