Apple security chief Ivan Krstić announced a new bug bounty program by the company that targets key areas of concern, including iCloud, Secure Boot, sandboxed processes and more at Black Hat security conference in Las Vegas Thursday.
According to Kristic, researchers can receive up to a $200,000 for their bugs depending on the severity. The program, however, is not open to just anyone. Invitations are initially being extended to a small handful of researchers who have previously reported significant vulnerabilities in Apple’s security.
While Apple expects to slowly grow the program over time, the bounties aren’t completely closed to those without an invitation. According to participants at Black Hat, Apple will extend offers to others no on the list, if a significant bug is reported.
While some researchers find the “invitation-only” route too restrictive, many believe Apple has made a wise decision in the slow roll-out.
“I personally think it’s a good start,” Rich Mogull, CEO of Securosis security firm wrote in a blog post about the program. “Apple didn’t need a program, but can certainly benefit from one. This won’t motivate the masses or those with ulterior motives, but it will reward researchers interested in putting in the extremely difficult work to discover and work through engineering some of the really scary classes of exploitable vulnerabilities.”
Apple has yet to release a list of researchers who have been invited to the program. According to several attendees at Apple's Black Hat 2016 presentation confirmed that invitations will be mailed in September.
In the meantime, several known security researchers who have focused their attention on Apple's ecosystem over the years are planning to meet informally with Apple's security team to discuss further details of the upcoming program. One such researcher is Will Strafach a.k.a @chronic. Strafach has a long history of studying Apple security, with deep ties in the jailbreak community. He was the founder of the Chronic Dev jailbreak team, which was responsible for early iOS jailbreak tools such as Greenpois0n for iOS 4.2.1 and Absinthe for iOS 5.1.1. He has since moved on to begin his own security firm, Sudo Security group, a mobile security firm specializing in enterprise mobile protection and app security evaluation.
“I’m very happy that they have done this,” Strafach told iDigitalTimes. “It will be great for device security moving forward and will absolutely incentivize reporting. There are quite a few people who just love hacking and exploiting bugs for the fun of it, but now that there is a dollar value attached, this can go from being a casual hobby to becoming something they can justifiably put a lot more time into.”
Other Black Hat participants mirrored Strafach's approval of Apple's upcoming bounty programming.
"It's definitely a step in the right direction in terms of rewarding researchers for their hard work and promoting more public research ," Azimuth security researcher Tarjei Mandt told iDigitalTimes. Mandt, along with colleagues David Wang and Mathew Solnik presented an Apple security talk themselves while at Black Hat.
Apple’s bug bounty comes as part of a general trend towards more collaboration with researchers outside of Apple’s official team.
In June, Apple for the first time left its kernel decrypted for developers to explore in the iOS 10 betas. According to Apple, allowing developers to see the kernel cache doesn’t give them any access to user info, but does allow for more eyes to examine it and report possible problems.
“By unencrypting it [the kernel] we’re able to optimize the operating system’s performance without compromising security,” an Apple spokesperson told TechCrunch.
Apple’s shift towards more transparency in security issues was likely pushed by its battle with the FBI over unlocking an iPhone used by the San Bernardino shooter. The FBI attempted to compel Apple to unlock the phone but later dropped its request after reportedly paying a third party nearly $1 million to break into the device.
Apple's Bug Bounty Program Rewards
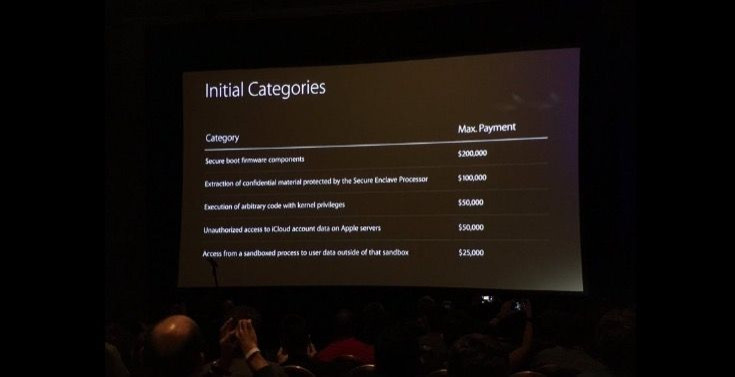
Apple’s Bug Bounty program is set to launch in September just in time for the release of its latest iOS 10 software and rumored iPhone 7. The categories for bounty rewards are as follows:
Vulnerabilities in secure boot firmware components: Up to $200,000
Vulnerabilities that allow extraction of confidential material from Secure Enclave: Up to $100,000
Executions of arbitrary or malicious code with kernel privileges: Up to $50,000
Access to iCloud account data on Apple servers: Up to $50,000
- Access from a sandboxed process to user data outside the sandbox: Up to $25,000


















