Cambridge University researchers revealed this week a flaw in Android phone factory reset that have put the sensitive information found on an estimated 500 million smartphones at risk.
According to a report released Thursday titled, Security Analysis of Android Factory Resets, the flawed factory reset on Android devices running older software doesn’t entirely wipe all data as was expected. This weakness has allowed researchers to recover a plethora of sensitive information from flashed devices including Facebook and Google login credentials, text messages, emails, contacts information and more. Even more startling is the fact that all this data could be accessed even if the user had been particularly diligent and turned on full disk encryption.
The study marks the first comprehensive look at the effectiveness of Android factory reset features and the results are more than a little concerning. While the factory reset option is meant to give users a peace of mind when trading in or selling their old devices, by allowing them to completely wipe the device and restore it to the factory settings, this study has proven that the system doesn’t function as expected in devices running Android 4.3 Jelly Bean and below.
Who Is Vulnerable To The Android Factory Reset Flaw?
The researchers tested the factory reset of 21 Android smartphones from five different manufacturers running Android 2.3.x to 4.3. All of the phones when tested did retain fragments of old data, including contact data stored in the phone app and third-party apps such as Facebook and What'sApp, images and video from the camera, and text-based conversations from SMS and e-mail apps. In addition, researchers were able to extract the master token on 80 percent of the devices, which gives access to extremely sensitive data such as Google log in credentials allowing access to Gmail and Google Calendar.
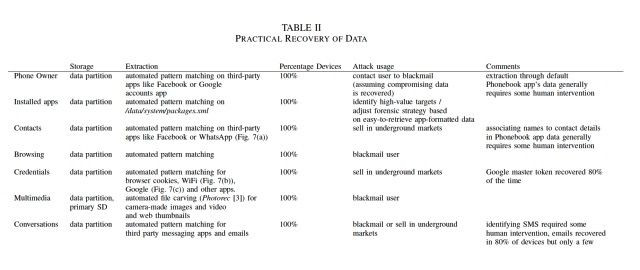
While researchers stressed the fact that they “never attempted to use [recovered] tokens to access anyone's account," the knowledge that they can be recovered is unsettling. Because of the widespread user of Android devices, researchers estimate some 500 million Android smartphones are at risk to this system restore flaw, which may not completely wipe disk partitions where sensitive data is stored. In addition, some estimated 630 million phones may not wipe internal SD cards which are used for storing pictures and video clips.
Even more concerning is the fact that data users assumed they had responsibly wiped from their devices could be recovered even in cases where full disk encryption had been in place, because, according to researchers, the file that stores the decryption key isn't erased during the factory-reset process.
The findings have some quite worrying implications for users wanting to sell or get rid of old Android devices as there is no way to ensure their data cannot be recovered. Thieves who know about the weakness and have some hacking skill could easily buy phones on sites such as eBay, and restore the wiped data in hopes of finding bank account information and other fraud related data.
While regular users are certainly at risk, devices that have belonged to corporations and were linked to systems storing sensitive corporate information will have the most to lose if these devices fall into the wrong hands. In addition, images and browsing histories be used for blackmail and credentials could also be sold off on the criminal hacking underground
How To Make Your Data Safe Before Getting Rid Of Your Old Android Phone
If you are planning to get rid of an old Android device, what is the best way to make sure your data is as safe from recovery as possible. At this point the best recommendation is to turn on full-disk encryption before getting rid of the device and adding a randomly generated password that includes numbers, upper- and lower-case letters, and symbols, and has a minimum of 11 characters. These kinds of passwords would be much more difficult to crack and require a lot more time, which would likely deter many from attempting it. There are a number of random password generating tools you can use in the Google Play store to help with that.
How to encrypt your Android device


















