Tuesday night MedStar Health announced some of their hospital systems had been hit with ransomware. They are yet another in a string of file-encrypting malware attacks against healthcare organizations in 2016.
In a statement posted on Facebook, MedStar Health revealed that its IT systems had undergone attacks early Monday morning that prevented users from logging in. Recognizing early signs of a ransomware attack, Medstar Health’s IT group was quick to take down all systems to stop further corruption. While the organization said they were making “significant progress toward restoring functionality” of its systems, the attacks are having a significant effect on operations, including requiring staff to revert to paper documentation until the issue is fully resolved.
“We will continue to partner with experts in the field of IT and cybersecurity, as well as law enforcement, to continually assess the situation as we safely restore functionality,” the organization wrote.
The ransomware attacks on Medstar Health are just another in a growing list of attacks striking health care organizations in the last month. As the popularity of the malware has grown, so has the size and significance of its targets. Attackers are using new and more sophisticated methods to deliver their malicious software that, in some cases, are causing victims to pay up rather than try to restore encrypted files themselves.

In a story iDigitalTimes broke Tuesday, Cisco Talos Senior Technical Leader Craig Williams revealed that dozens of health care organizations and been infected with SamSam ransomware in just the last week. The attacks were significant because they utilized a new method of infection not seen before. Instead of requiring an individual to click on a link in an email or browser page, the ransomware infected systems via an unpatched server vulnerability. According to Williams, the attackers used a public vulnerability that has a patch available. Systems attacked by the SamSam ransomware become vulnerable because the servers had not been kept up-to-date. While Williams doesn’t believe attackers are specifically targeting healthcare organizations, they may be susceptible due to lacking information security infrastructure.
“The frustrating thing about this is, in order to mitigate it all you have to do is follow standard best practices. Patch your servers. Have a backup. It’s that simple,” Williams told iDigitalTimes. “A lot of people in the health industry don’t have proper administrators or a security staff so as a result things like backups aren’t happening. We think attackers are striking health care because it’s an industry that will pay and has poor information security structure.”
In the last month, two separate hospitals, Hollywood Presbyterian California and Methodist Hospital in Kentucky, each reported paying out $17,000 in bitcoin to have files decrypted.
As for the cybercriminals behind SamSam ransomware, they appear to be milking the situation for all its worth. According to the Cisco Talos team, which has been monitoring SamSam ransomware infections, the attackers have begun pressing victims for larger ransoms.
“We have started to see changes in the amount and types of payment options available to victims. Initially, we saw a payment option of 1 bitcoin for each PC that has been infected,” the company wrote. “Later we saw the price for a single system has been raised to 1.5 bitcoin… they even added an option for bulk decryption of 22 bitcoin (about $10,000 at the time of writing) to decrypt all infected systems.”
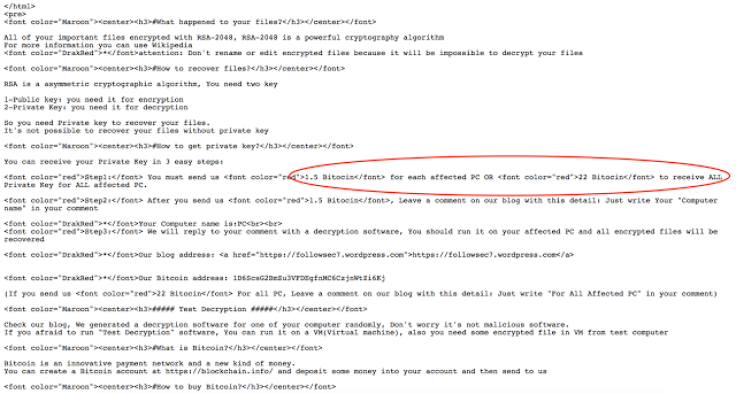
The company believes the malware author may be trying to see how much people will pay to have their files decrypted, a disturbing thought for those dealing with these kinds of attacks.
While several healthcare organizations hit with ransomware have refused to pay, the cost in manhours to restore what attackers encrypt could outweigh the cost of paying the ransom.
According to Barry Gregg, a controller for a flooring company in Austin, Texas that was recently hit by Locky ransomware, even if IT teams work swiftly, such attacks can be costly to recover from.
Gregg’s company was hit by Locky ransomware in late February, and though the IT team shut down the malware within an hour of it hitting the system, it managed to encrypt over 3,000 files stored on the company’s server. Fortunately the company had a good backup system in place and very little data was lost, but the cost of cleaning up the mess was significant.
“It took us a good 24 hours to restore everything,” said Gregg. “With tech support working overnight and me being available overnight, it would have been cheaper for us to just pay the ransom. But if you do that, you just get labeled as a sucker and are definitely on the hit list again.”
The willingness of some hospitals to give in to ransomware attackers’ demands may also be contributing to a rise in attacks. For this reason, security firms urge victims of ransomware not to pay.
“Ransomware is a growing trend in the criminal underground because it is so profitable,” Trend Micro VP, Mark Nunnikoven told iDigitalTimes. “When your job is on the line and critical data at stake, it’s tempting to pay the ransom, but this only makes you a bigger target.”