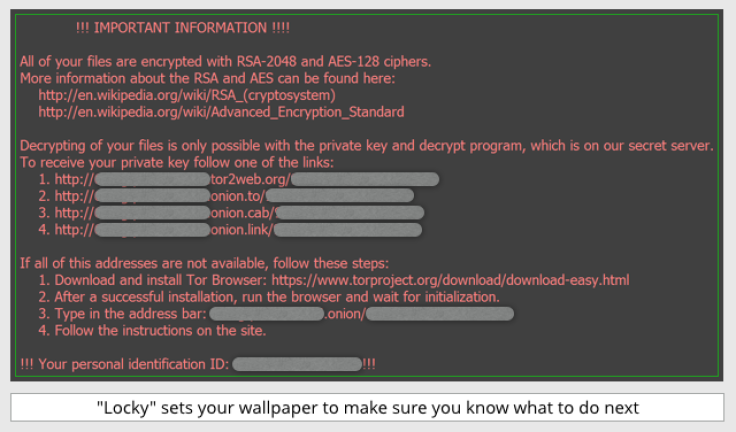
A new Cryptolocker-type ransomware called “Locky” has been spreading like wildfire to users around the globe. Can the file-encrypting virus be removed and files restored? Find out everything you need to know about the new malware, here.
The Locky virus, a new ransomware the encrypts users’ files and demands bitcoin payments to decrypt them, made an impressive debut Tuesday when it was discovered by security researchers at PhishMe. The ransomware attack, which was first sent to nearly half a million victims on February 16, came in the form of a Word document with a malicious macro in it. Targets were sent the infected document via an email, which led them to believe the document was an invoice requiring payment. When the document was opened, it requested permission to run a Macro, which many victims allowed. The infected macro then performed the dirty work of installing the ransomware and scrambling the victims’ files.
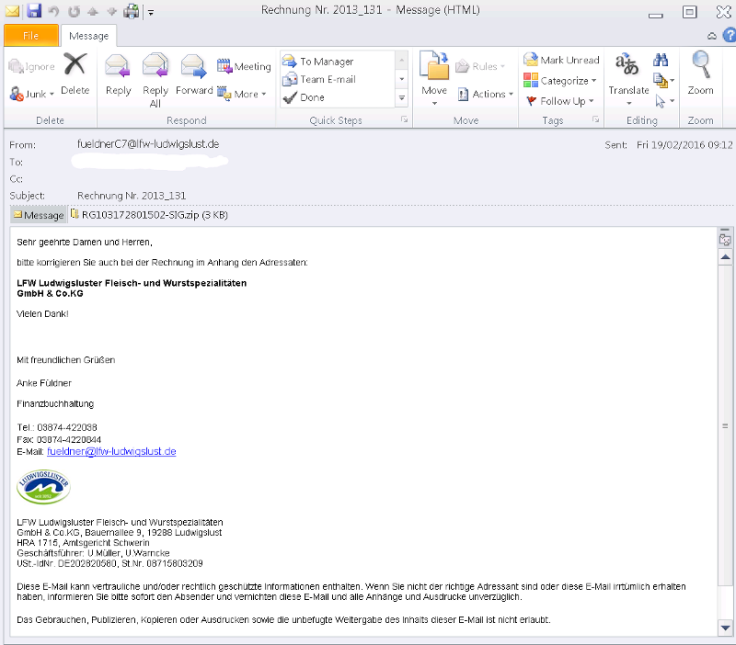
How Many Victims Has The Locky Ransomware Virus Taken?
While the first Locky attack on Tuesday targeted 400,000 victims, it was only a trial run for the malware, says security researcher, Kevin Beaumont. Over the last two days, the active infections have ramped up quickly and continue to rise.
Beaumont, who was able to tap into traffic from the Locky virus, shared his findings in a blog post on Medium, and frankly, they’re alarming. According to Beaumont, Locky is infecting anywhere from one to five computers every second, making the new ransomware a “major cybersecurity incident.” If the trend continues, up to a quarter of a million computers could be infected in just three days, the researcher wrote.
iDigitalTimes reached out to Beaumont for updates on the Locky infections he’s been following. In the last 24 hours, the researcher has tracked nearly 60,000 newly infected computers, the majority found in Germany and the United States.
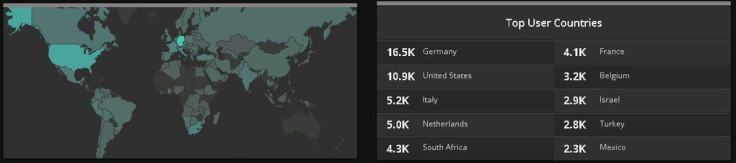
But this number is only part of the larger picture, Beaumont claims. The researcher owns three of the domains that the Locky ransomware is using, allowing him to track infections coming from those domains.
“When they [victims’ computers] get infected, they check in,” said Beaumont.
But since the number of domains the file-encrypting malware uses is unknown, the number of infections happening could be much larger.
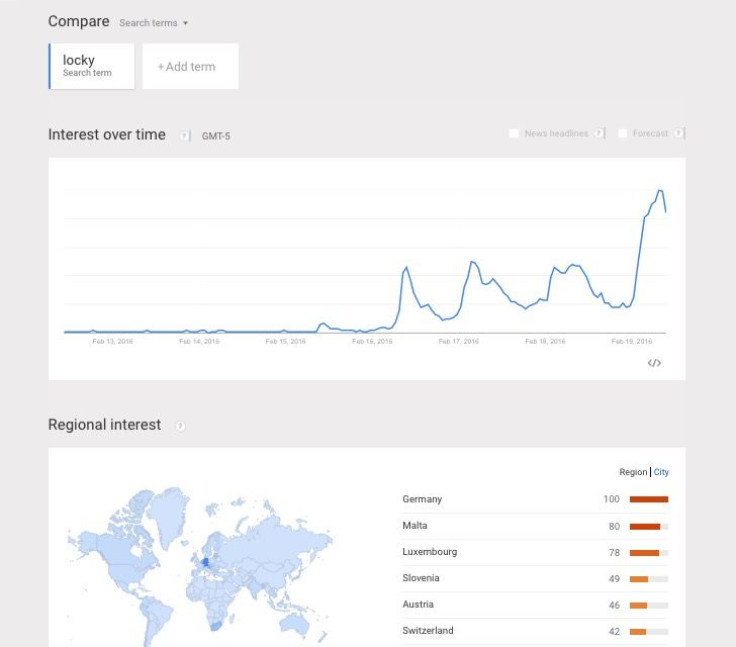
Google trends data on the keyword “Locky” shows a dramatic increase in traffic over the last 24 hours, with the largest number of queries coming from Western European countries like Germany, Malta and Luxembourg.
How Locky Works
Locky ransomware begins its attacks from an infected Windows machine but can spread to other platforms like Linux and OS X via network connections. The ransomware encrypts a wide range of file types, Naked Security researchers wrote in a blog about Locky, including but not limited to videos, images, PDFs, program source code, and Office files. This includes files in any directory on any mounted drive that the infected computer can access, such as removable drives that are plugged in at the time or network shares that are accessible like servers and other people's computers -- no matter if they are running Windows, OS X or Linux. If an infected user is connected to a network with administrator controls, the damage can be significantly widespread. Locky also encrypts Bitcoin wallet files if users have them, making it impossible to access the Bitcoin users may have stored. While losing files is bad enough, the loss of a Bitcoin wallet makes victims even more willing to pay the ransom, particularly if the price of the ransom is less than the value of the Bitcoin stored in the encrypted wallets.
NEW: Cryptolocker, Locky Ransomware Installers Can Now Infect Computers Without Users Clicking Anything, Say Researchers
But Locky ups the ante even further, taking additional steps to bring victims to their knees. Once installed, the ransomware removes any Volume Snapshot Service (VSS) files or “shadow copies,” that users’ computers may have made. These shadow copies are a way Windows makes live backup snapshots of works in progress so if users forget to save, or the computer is unexpectedly shut down, those files can be recovered. Users can become dependent on the mechanism as their main backup and neglect making real backups. With a sophisticated ransomware like Locky on the loose, many victims may find themselves at the mercy of the attackers and could soon be shelling out the .5 – 1.00 Bitcoin (approximately $400) to get their files restored and the malware removed.
Can The Locky Ransomware Virus Be Removed And Files Decrypted Without Paying A Ransom?
At this point, there is only one method of removing the Locky virus and having files decrypted: paying the ransom. Furthermore, Beaumont believes there’s little likelihood a tool will be developed that can decrypt files Locky has scrambled.
“Locky is very well designed,” Beaumont told iDigitalTimes. “The encryption uses a server infrastructure which is resilient and difficult to take down for authorities as there are backup systems in place. The malware uses strong encryption as well and unless a big flaw is found in the attacker's methodology, people are best restoring from any backups they may have.”
The Rise Of Ransomware

Ransomware infections have been steadily rising over the last two years and are expected to continue growing in 2016 . Having initially targeted individuals or small businesses, ransomware attacks have grown increasingly more sophisticated, with larger targets coming into focus. In the last week, news broke that a major medical institution, Hollywood Presbyterian Medical Center , has been held hostage by ransomware attackers and was left no alternative but to pay up the demand 40 bitcoins, worth $17,000 .
While there was no indication of whether law enforcement counseled the hospital to pay the ransom, TrustedSec CEO David Kennedy told CBS News the decision likely came because the hospital had a poor backup system.
“If they decided to pay the ransom, it probably means that they didn't have very good backups, they weren't able to recover the data, and that the data would have been lost if they didn't pay the ransom," said Kennedy.
With so much sensitive information at the mercy of hackers, hospitals, schools or other government-related institutions have a lot to lose if such files cannot be recovered.
How To Prevent Ransomware Attacks
The rise of ransomware attacks highlights the need for users of all kinds to take greater security precautions with their stored data. Security firm, Malwarebytes , maker of malware detection tools and anti-virus software, have been actively working on a new product that combats ransomware attacks. The Malwarebytes Anti-Ransomware software is currently in beta testing which users can sign up for at Malwarebytes’ official website. In addition, Naked Security researchers offer users a number of useful tips for avoiding ransomware infections, the most important of which include making regular backups that are stored offline, updating your computer on schedule, limiting admin login on an "as needed" basis and using a Microsoft viewer application to inspect documents before opening. You can also download a VPN to encrypt your network data, which would help prevent potential data leaks and theft of your private information. For a complete list of the tips visit Naked Security’s official blog.