The San Francisco transit system was hacked by HDDCryptor ransomware this weekend as thousands of machines on the system went down, yielding free rides to passengers Saturday. Find out more about the attack and who was behind it.
Ransomware has become a favorite tool amongst cyber criminals as victims ranging from small family businesses to massive healthcare organizations have become intimately acquainted with the ransom-demanding malware. Over the weekend, attackers made the San Francisco transit system (SFMTA) the object of their nefarious designs, as hackers claimed control over 2,112 of its 8,656 networked computer systems, demanding a ransom of 100 bitcoin, which equals approximately $70,000.
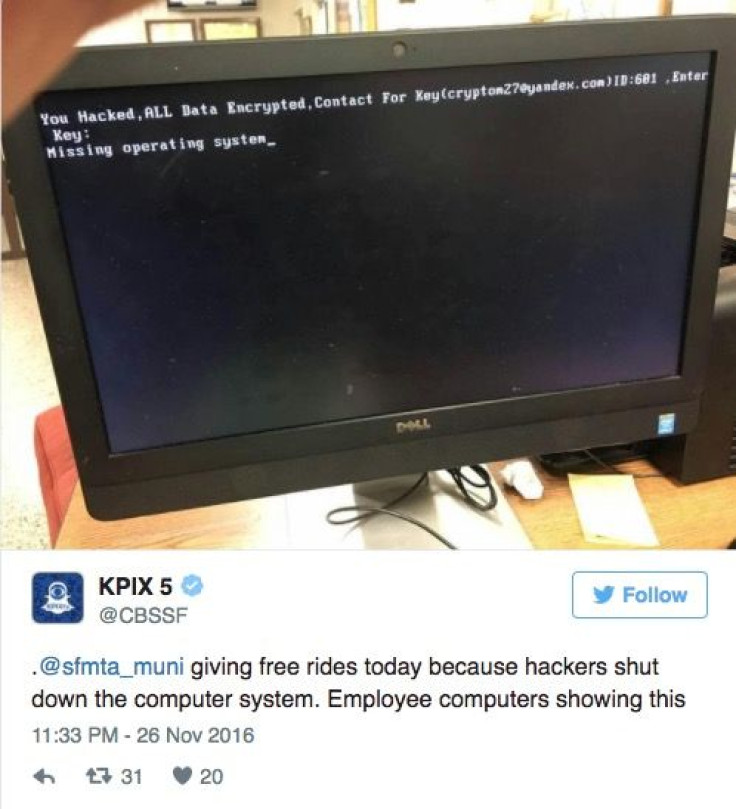
The attack was first reported Friday night when an unusual message appeared on San Francisco Muni station computer screens across the city.
“You Hacked, ALL Data Encrypted,” the message read.

Following the cryptic message, Muni riders at ticket machines Saturday morning were told the system was out of order and that all rides were free.
When questioned about the attack, t he SFMTA was hesitant to confirm it as a hack. While insiders told CBS San Francisco that the system had been hacked for days, spokesperson Paul Rose refused to confirm such reports. According to Rose, the SFMTA was conducting an ongoing investigation and that while there had been “no impact to the transit service” they had decided to “open the fare gates as a precaution to minimize customer impact.”
By Sunday evening, the San Francisco transit system appeared to be back online but no additional details were given as to whether the ransom was paid or not.
Who Was Behind The San Francisco Transit System Ransomware Attack? How Much Damage Was Done?
The attackers behind the San Francisco transit system hack are not new to using ransomware. At the time of the attack, the AFMTA was given the email, cryptom27@yandex.com as a contact point. The address has frequently been used by ransomware-leveraging cyber criminals to communicate with victims and give instructions for encryption key payment to unlock encrypted files.
According to Hoodline , the SFMTA made contact with the attackers via the given email, at which time they identified themselves as “ Andy Saolis,” a pseudonym often used by attackers who use the HDDCryptor ransomware. In the email, the attacker explained that the hack wasn’t targeted, but rather used to show the weaknesses in the SMFTA system.
“We don’t attention to interview and propagate news,” the email read. “Our software working completely automatically and we don’t have targeted attack to anywhere! SFMTA network was Very Open and 2000 Server/PC infected by software! So we are waiting for contact any responsible person in SFMTA but I think they don’t want deal! So we close this email tomorrow!”
So far no details have been revealed about how the system was infected, but security experts speculate that the ransomware was likely spread from an administrator machine, which may have fallen victim to an email phishing scam. HDDCryptor a.k.a. Mamba ransomware, is a relatively new as it was first discovered back in September, and is a unique form of ransomware in that it not only encrypts files and folders on local drives, removable media or network shares, it actually locks drives themselves, making it impossible to access or store anything on the locked drives.
Of the 2112 computers attackers listed as compromised, Hoodline reports that none of them appear to be part of the San Francisco transit systems’ backup servers, which may have been why they were able to get the system back online without paying out a ransom.
Though the transit system has gone back online, the extent of damage caused by the attacks has yet to be quantified. According to the BBC, the computers listed in the hack included employee terminals as well as machines that may be used to look after payroll and employees’ personal information. It is unclear what information may have been compromised or lost due to the attack.
As more information is learned, we’ll be sure to update this report.